Reyee EG PoC Guide V1.0

Please rate this document.
Please leave your suggestions here.
If Ruijie may contact you for more details, please leave your contact information here.
* I understand and agree to Terms of Use and acknowledge Ruijie's Privacy Policy.

Thank you for your feedback!

. Gateway TestingLists
1.1 Management
1.1.1 eWEB
| Testing project | eWeb |
| Testing purpose | Enable WEB and log into Gateway successfully |
| Testing procedure and expected results |
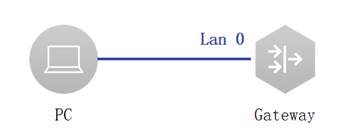
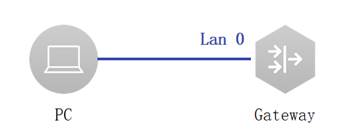
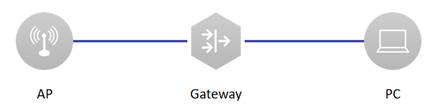
1. Connect PC with Gateway through net cable as shown above. (in this example, port LAN 0 is connected) 2. PC will get IP by DHCP when connect LAN 0. (in this example, DHCP server was set on Gateway) 3. Enter the default IP of Gateway 192.168.110.1 in browser. (the default IP of Gateway is 192.168.110.1 or 10.44.77.254. in this example, the Gateway IP is 192.168.110.1) browser must be IE and other major browsers and open compatible mode. 4. Verify Web access. (Expected interface is shown below.)
|
| Measured record | Login eWeb successfully. |
| Testing conclusion | eWeb can be opened by simply enter 192.168.110.1 via browser. |
1.2 Basic Feature
1.2.1 DHCP Server
| Testing project | DHCP Server |
| Testing purpose | Enable service DHCP and create IP Pool. Test to confirm whether PC can obtain IP address successfully. |
| Testing procedure and expected results |
1. Enable DHCP Serve and create IP Pool via eWeb
2. PC can obtain IP address.
|
| Measured record | PC can obtain IP address. Show the user IP details on EG DHCP online user list. |
| Testing conclusion | DHCP server can assign IP address to each device successfully. |
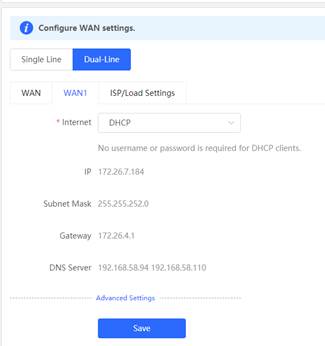
1.2.2 WAN uplink
| Testing project | WAN uplink |
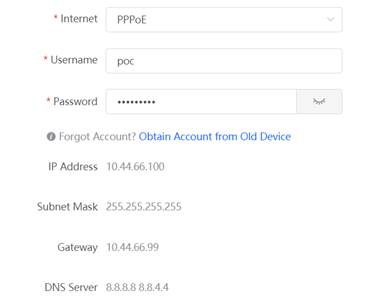
| Testing purpose | The WAN port can get IP by DHCP or Static or PPPoE Test to confirm the Gateway can access the internet |
| Testing procedure and expected results |
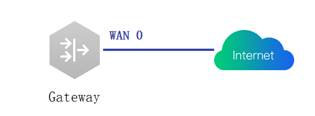
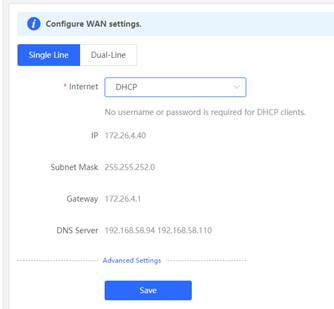
1. Open the WAN configuration and set internet DHCP via Gateway eWeb
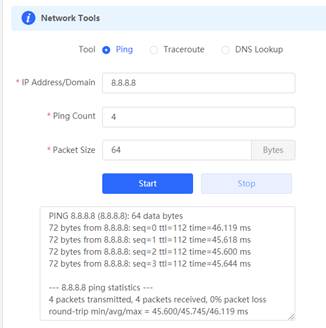
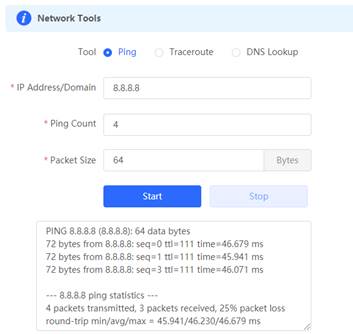
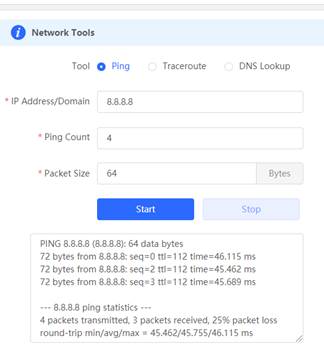
2. Ping 8.8.8.8 via Gateway eWeb, Expected results: ping successfully.
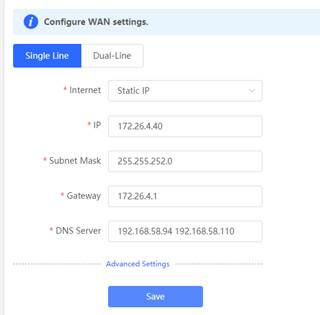
3. Set the internet static IP on WAN configuration via Gateway eWeb
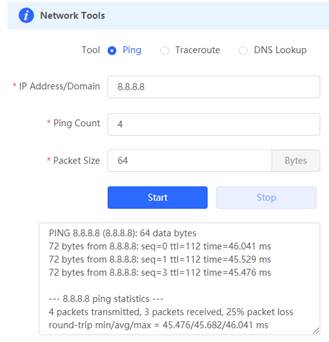
4. Ping 8.8.8.8 via Gateway eWeb, Expected results: ping successfully.
5. Set the internet PPPoE on WAN configuration via Gateway eWeb
6. Ping 8.8.8.8 via Gateway eWeb, Expected results: ping successfully
|
| Measured record | Ensure the obtained IP can access the internet when choose any one of them. (DHCP, Static IP, PPPoE) When choose PPPoE should have the PPPoE Server. |
| Testing conclusion | Gateway can access the internet by WAN setting via Gateway eWeb. |
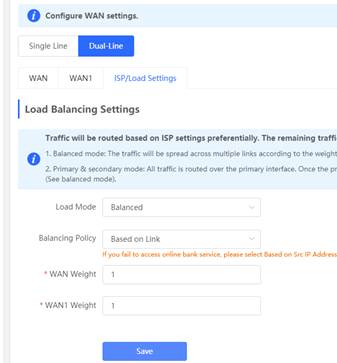
1.2.3 Dual-WAN uplink
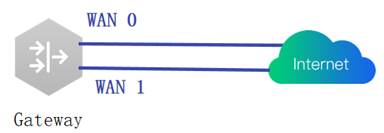
| Testing project | Dual-WAN uplink |
| Testing purpose | Enable Dual-WAN uplink on Gateway Test to check if there is traffic passing on Dual-WAN uplink |
| Testing procedure and expected results |
Note: 1. Balanced mode: The traffic will be spread across multiple links according to the weight of each WAN port. For example, if WAN and WAN1 weight are set to 3 and 2 respectively, 60% of the total traffic will be routed over WAN and 40% over WAN1 2. Primary & secondary mode: All traffic is routed over the primary interface. Once the primary interface fails, traffic will be switched over to the secondary interface. If there are multiple primary and secondary interfaces, please configure their weight (See balanced mode)
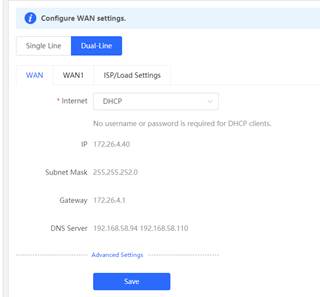
1. Open the Dual-Line configuration page via Gateway eWeb
2. Set load balance on Dual-Wan uplink
3. Ping 8.8.8.8 via Gateway eWeb, Expected results: ping successfully
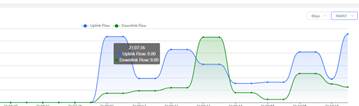
4. Check the real traffic flow from Overview option via Gateway eWeb, Expected results: traffic pass Dual-WAN
|
| Measured record | When the balancing policy is selected as Scr-IP and the entire network has only the same IP network segment, only one wan port can be seen |
| Testing conclusion | Dual-Wan can effectively provide more link bandwidth and link redundancy |
1.2.4 LAN Port VLAN
| Testing project | LAN Port VLAN |
| Testing purpose | Enable to tag VLAN on LAN port Test to confirm whether tag VLAN on LAN port is available by DHCP |
| Testing procedure and expected results |
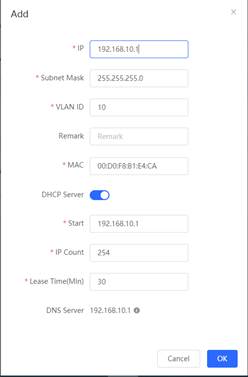
1. Enable DHCP Server and create IP Pool for VLAN 10 via eWeb
2. Open LAN Port VLAN configuration page from Port Menu.
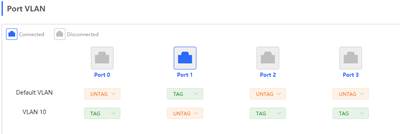
3. Untag VLAN 10 on port LAN 1
NOTE: UNTAG:The port does not carry the VLAN tag when sending the packets, similar to the native VLAN configuration of the switch TAG: The packets corresponding to the VLAN sent from the port will carry the VLAN tag, similar to the non-native VLAN of the trunk port Not Join:The port does not belong to the VLAN and does not participate in the forwarding of the VLAN packet, which is removing the VLAN when configuring the allow VLAN under the trunk
4. The PC can obtain the IP 192.168.10.X
|
| Measured record | The UNTAG VLAN means set the native VLAN on port |
| Testing conclusion | LAN Port VLAN can used for DHCP to let user get different IP sub-net network. |
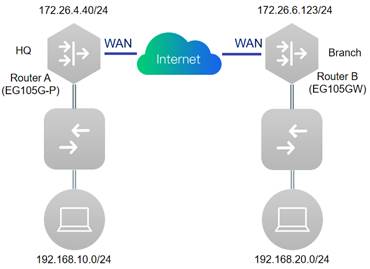
1.2.5 IPsec VPN
| Testing project | IPsec VPN | ||||||||||||||||||||||||
| Testing purpose | Successful establishment of IPsec VPN between routers | ||||||||||||||||||||||||
| Testing procedure and expected results |
Note: If the IPsec VPN server is under the NAT device, need configure the port-mapping, udp port 500 and 4500.
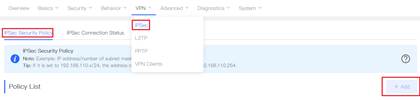
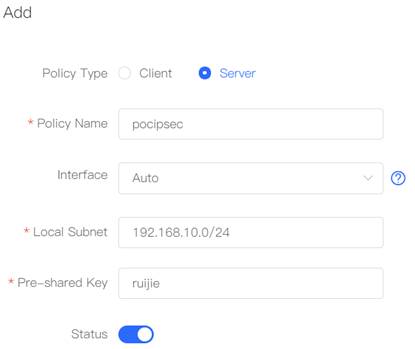
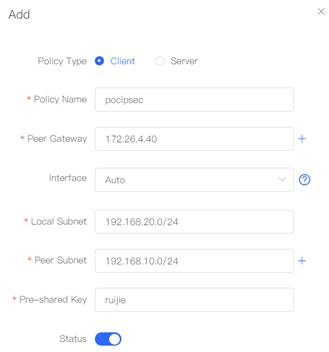
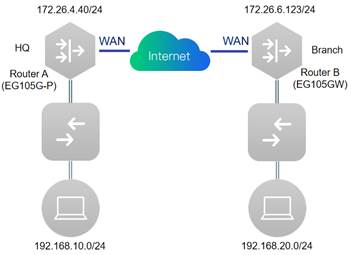
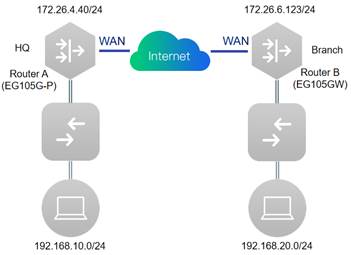
1. Configure Router A in the HQ as the IPsec server. Choose VPN→IPSec click “Add” to add a policy.
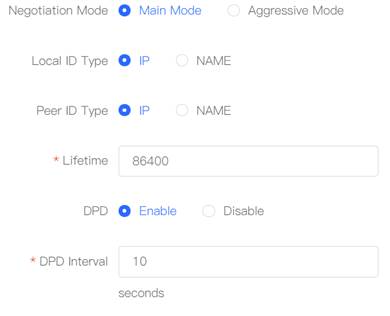
4. Set the "Connection Policy".
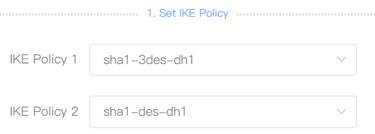
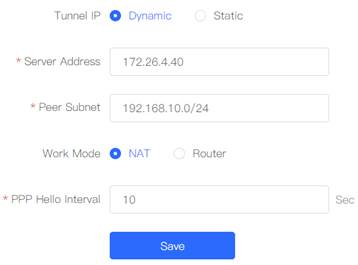
5. Configure Router B in the Branch as the IPSec client. Select Policy Type as "Client", Fill in the Policy Name, Peer Gateway (HQ’s public IP address or domain), Local Subnet, Peer Subnet, and Pre-share Key (need to be the same as HQ’s key). 6. Set "IKE Policy"
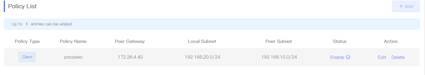
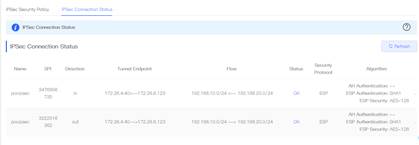
and “Connection Policy” the same as for HQ. You can see the completed configuration entries in the Policy List 7. Check the connection establishment status in Router A's IPSec Connection Status
page. The image below shows "OK" for "Status", which means that IPsec VPN was successfully created. 8. Testing connectivity to HQ at Router B
| ||||||||||||||||||||||||
| Measured record | Establishment of IPsec VPN between EG105G-P and EG105GW | ||||||||||||||||||||||||
| Testing conclusion | Reyee EG can be used as IPSec server and client | ||||||||||||||||||||||||
1.2.6 L2TP VPN
| Testing project | L2TP VPN | |||||||||||||||
| Testing purpose | Successful in establishing L2TP VPN between routers | |||||||||||||||
| Testing procedure and expected results | Note: If the L2TP VPN server is under the NAT device, need configure the port-mapping, udp port 1701.
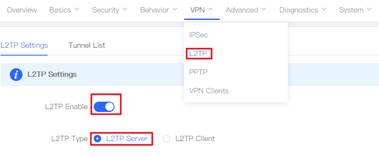
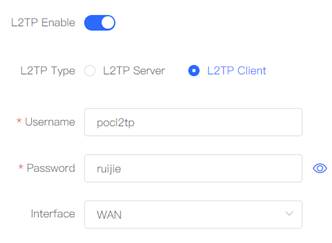
1. Configure Router A in the HQ as the L2TP server. Choose VPN→L2TP, turn on L2TP Enable and select L2TP Type as L2TP Server. 2.
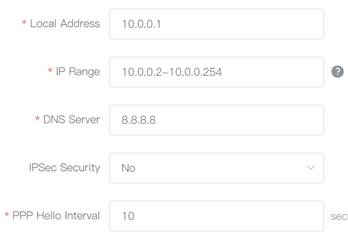
Fill in the local tunnel address, tunnel IP address range, DNS Server.
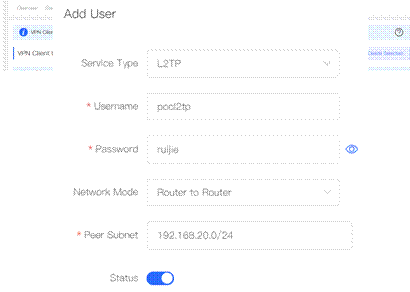
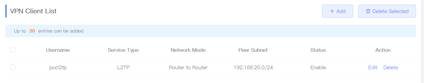
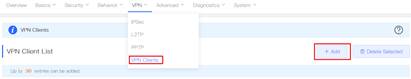
3. Create VPN clients. VPN→VPN Clients, click "Add" to add client. 4. 5.
6.
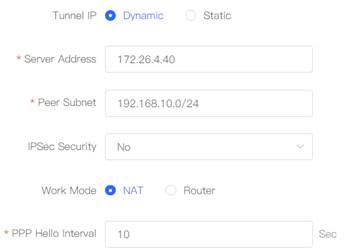
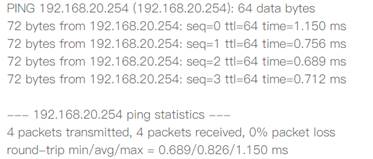
Select the tunnel IP as Dynamic, fill in the server address, Peer Subnet. 7. Check the tunnel establishment status in the Tunnel List page of Router B. As shown in the figure below, the tunnel IP was obtained, and the tunnel was successfully established.
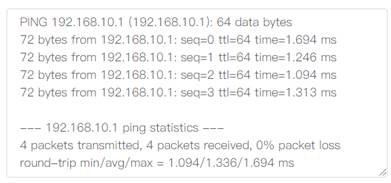
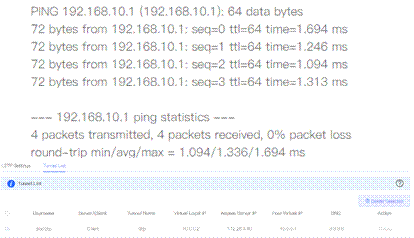
8. Testing connectivity to HQ at Router B.
| |||||||||||||||
| Measured record | Establishment of L2TP VPN between EG105G-P and EG105GW | |||||||||||||||
| Testing conclusion | Reyee EG can be used as L2TP server and client |
1.2.7 PPTP VPN
| Testing project | PPTP VPN | |||||||||
| Testing purpose | Successful in establishing PPTP VPN between routers | |||||||||
| Testing procedure and expected results | NOTE: If the PPTP VPN server is under the NAT device, need configure the port-mapping, udp port 1723.
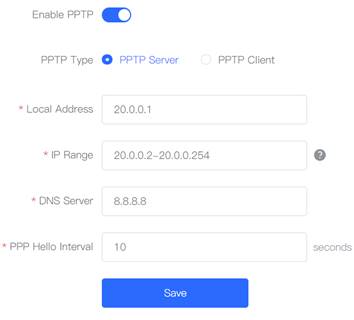
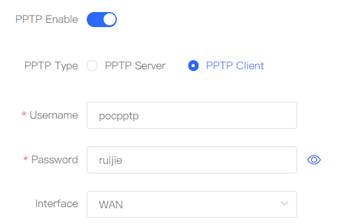
1. Configure Router A in the HQ as the PPTP server. Choose VPN→PPTP. 2. Select PPTP Type as PPTP Server, fill in the local tunnel address, tunnel IP address range, DNS Server
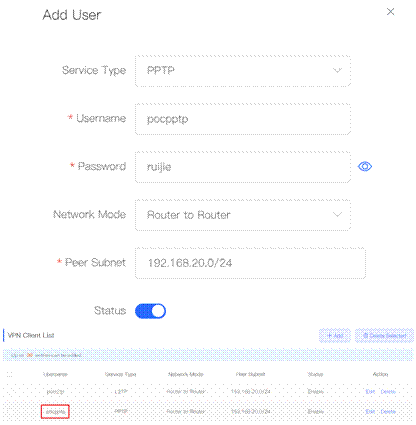
3. Create VPN clients.
| |||||||||
|
|
4. Select the Service Type and Network Mode, fill in the Username, Password and Peer Subnet.
5. Configure Router B in the Branch as the PPTP client, fill in username and password.
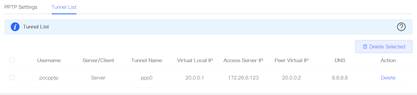
6. Select the tunnel IP as Dynamic, fill in the server address, Peer Subnet. 7.
8. Testing connectivity to Branch at Router A.
| |||||||||
| Measured record | Establishment of PPTP VPN between EG105G-P and EG105GW | |||||||||
| Testing conclusion | Reyee EG can be used as PPTP server and client |
1.2.8 Flow Control
| Testing project | Flow Control |
| Testing purpose | Set a limit to Control the total or individual traffic flow of clients |
| Testing procedure and expected results |
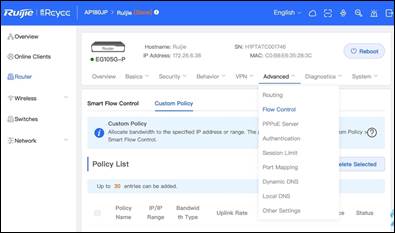
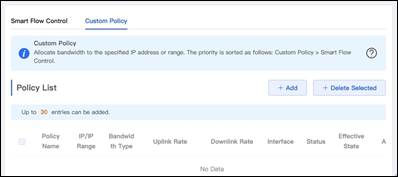
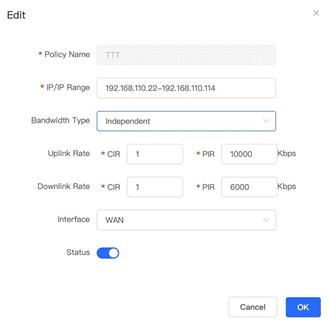
1, To enable Flow Control feature, we need to first open Router >> Advanced >> Flow Control tap as shown below.
2. Then in Custom Policy tap click + Add.
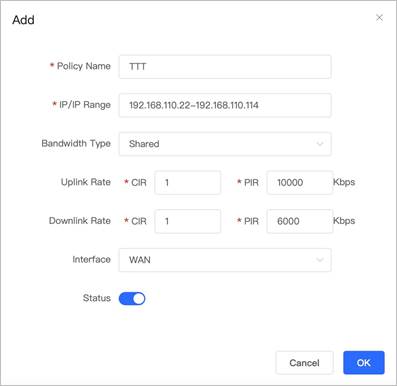
3. Enter the Policy Name, IP/IP Range and limits for Uplink / Downlink Rate.
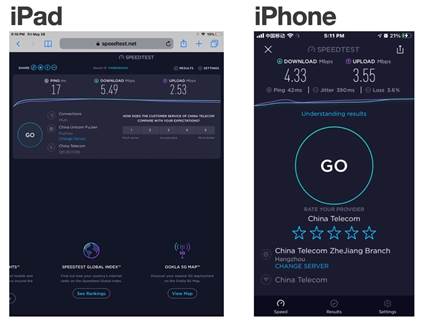
4. Now for experimental purpose, we will use two devices (one iPhone and one iPad) to do traffic flow rate test ( via either speedtest.net or Speedtest App from App Store). Expected results: The sum of traffic flow from iPhone and iPad will be close to the limits we set.
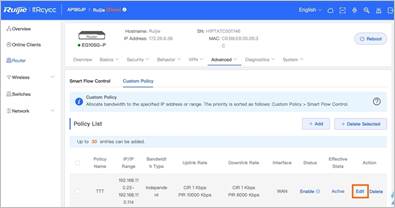
5. For comparison, now we change one setting by click Edit. In Edit tap, change Bandwidth Type from Shared to Independent
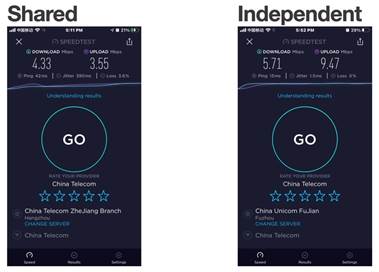
6. Do the speed test again and compare the results.
From this speed test we can see that speed of traffic flow on iPhone jumped conspicuously from 4.33 to 5.71 for Download and from 3.55 to 9.47 for Upload. |
| Measured record | The noticeable changes of traffic flow speed as shown above verified the Flow Control feature in Reyee Wireless can be handled easily and intuitively. |
| Testing conclusion | With Flow Control configured, the sum or individual boundary of traffic flow can be controlled. |
1.3 Behavior
1.3.1 APP control
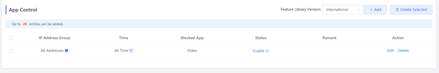
| Testing project | APP control |
| Testing purpose | Test app management on Gateway |
| Testing procedure and expected results |
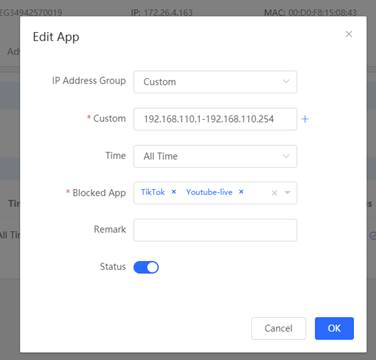
1. Ensure that the user can get 192.168.110.X 2. Open the APP control configuration page and add the control
3. Open the APP to check if can block Tik Tok and YouTube.
|
| Measured record | Record the test result for website and APP |
| Testing conclusion | The APP can be blocked |
1.3.2 Websitemanagement
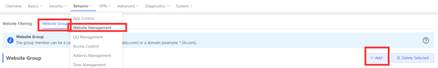
| Testing project | Website management |
| Testing purpose | Enable Website management on Gateway Test to block the website. |
| Testing procedure and expected results |
1. The PC get the 192.168.110.X from Gateway
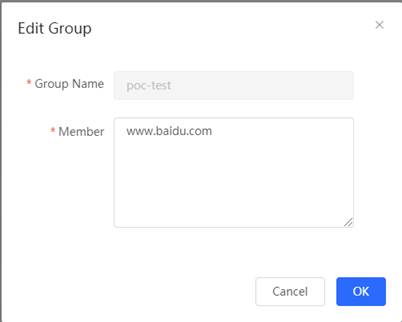
2. Open the Website management configuration page and add the website group you want to block.
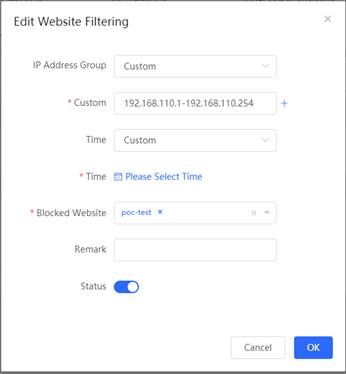
3. Set the website filtering
4. Access the website to test if it is blocked. |
| Measured record | The IP address obtained by the user must be the same as the configured IP address on website filtering. |
| Testing conclusion | The website can be blocked. It’s best to be able to display blocking slogans. |
1.3.3 Access control
| Testing project | Access Control |
| Testing purpose | Create ACL(IP-base and MAC-base) to achieve the effect of access control. |
| Testing procedure and expected results |
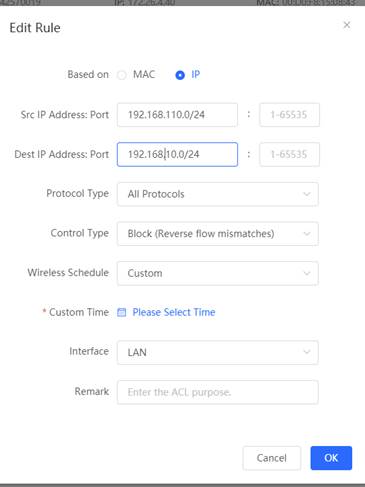
1. AP get 192.168.110.x and PC get 192.168.10.x 2. Create IP-based ACL to deny PC access the AP
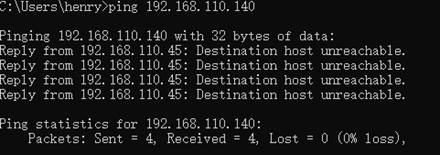
3. PC ping AP to test if the ACL is applied. The below picture shows that cannot connect to port
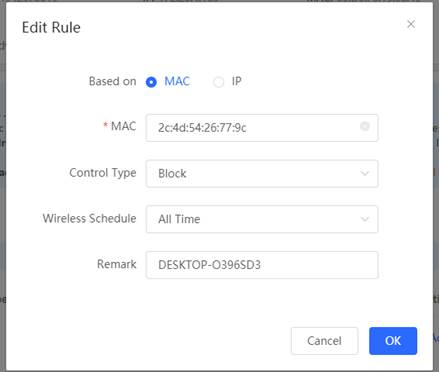
4. Create MAC-base ACL to deny PC access the internet (MAC-base default applied on WAN port)
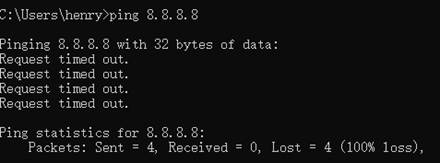
5. Use PC access the internet. (ping 8.8.8.8) The below picture shows that ping timeout.
|
| Measured record | ACL can only control one-way. (Means reverse flow mismatch) |
| Testing conclusion | Access control can be used on Gateway |
1.4Authentication
1.4.1 CloudAuth (Voucher/Account/one-click)
| Testing project | Cloud Auth (Voucher/Account/one-click) |
| Testing purpose | Enable Cloud Auth (Voucher/Account/one-click) on gateway |
| Testing procedure and expected results |
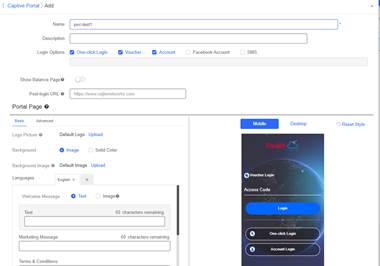
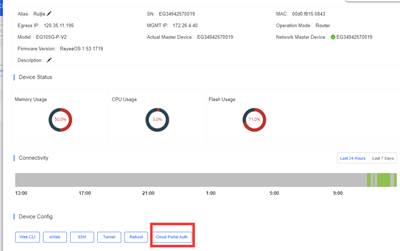
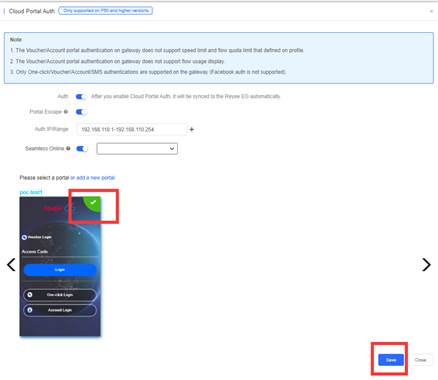
1. Ensure that the AP and Gateway online on cloud. 2. Create captive portal on cloud and apply on EG
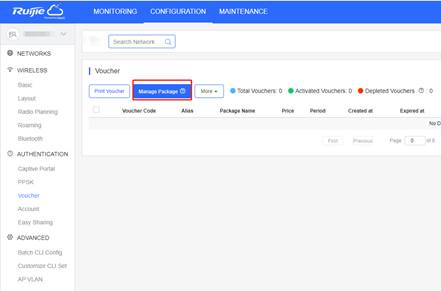
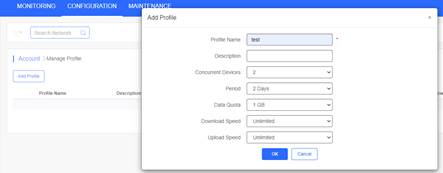
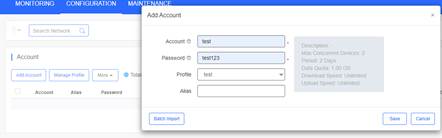
3. Create Account and Voucher on Cloud
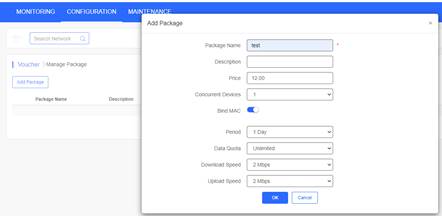
Add a voucher package
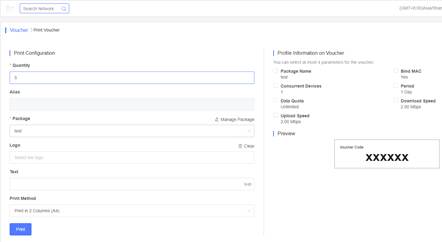
Print the voucher code
Add the account profile
Add the account and the password
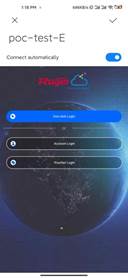
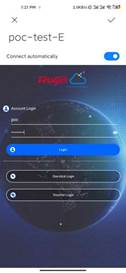
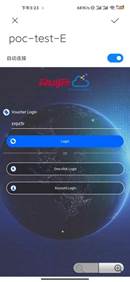
4. Use phone connect SSID to test Account/Voucher/One-click
|
| Measured record | When use one terminal to test auth should forget network and kick off the user (for example Account auth success and then want to Voucher auth, should do this step) |
| Testing conclusion | The Account/Voucher/One-click can use on cloud authentication |
1.5 Advanced
1.3.1 Port mapping
| Testing project | Port mapping |
| Testing purpose | Enable Port mapping on Gateway (Extra-net users can access the web configuration interface of intranet devices) |
| Testing procedure and expected results |
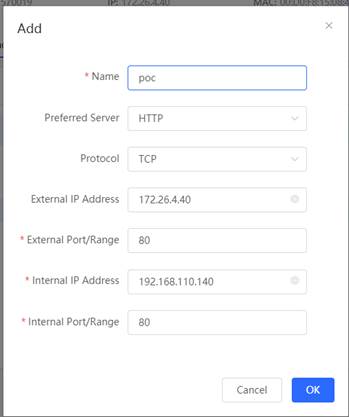
1. AP get the Intranet address 192.168.110.140 and PC get the Internet address 172.26.4.1.(Simulate extra-net users with PC) 2. Open the Port mapping configuration page and configure. (EG’s external network export address is 172.26.4.40)
3. Test to login the Ruijie AP by web (Enter 192.168.110.140 on browser.), Reyee AP can’t support login the eWeb from WAN
|
| Measured record | This example just to test login web, so mapped to port 80. Can map the port you want to use |
| Testing conclusion | Port mapping can be used on Gateway |
1.3.2 Packet capture
| Testing project | Packet capture |
| Testing purpose | Enable Packet capture on gateway Test to confirm that can capture the ping packet |
| Testing procedure and expected results |
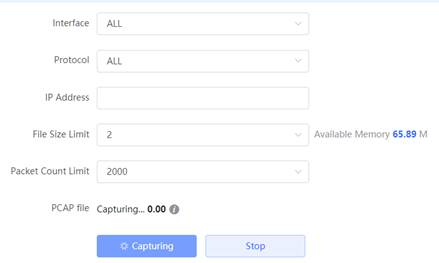
1. PC obtain the 192.168.110.236 IP from gateway and ping 8.8.8.8 2. Open the packet capture configuration page and start capture It is best to enable capture and then ping, to be able to capture the entire process of ping interaction
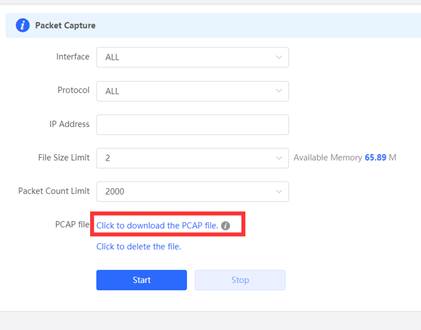
3. Click download PACP file when stop capture
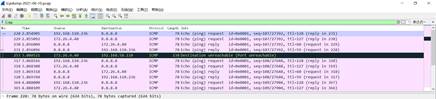
4. Open the PCAP file and choose the ICMP to confirm whether capture the ping packet.
|
| Measured record | If want to capture more precise packets, need to add the conditions on the packet configuration page for capturing packets |
| Testing conclusion | It is easier to achieve the capture packet on gateway |
1.3.3 PPPoE Server
| Testing project | PPPoE Server |
| Testing purpose | PPPoE Server test |
| Testing procedure and expected results |
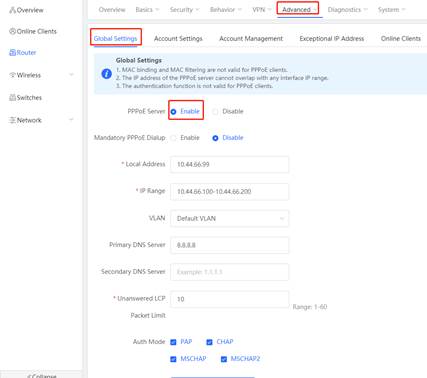
1. Enable the PPPoE Server, configure the Local address and IP Range, based on the scenario, choose the VLAN
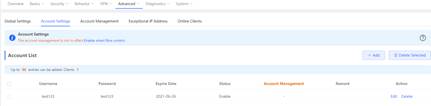
2. Create the PPPoE account
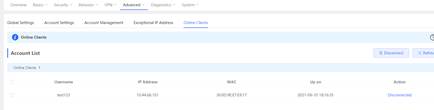
3. Check the online users and status
|
| Measured record | PC connect to the EG and set the PPPoE configuration, with the correct username and password, pc obtain the IP address and access to the internet |
| Testing conclusion | EG support PPPoE server feature |